SlowMist: The Hacker's Techniques and Questions Behind the Nearly $1.5 Billion Bybit Hack
Original Article Title: "The Hacker Technique and Questions Behind the Nearly $1.5 Billion Bybit Hack"
Original Source: SlowMist Technology
Background
On the evening of February 21, 2025, Beijing time, according to on-chain detective ZachXBT, a large-scale fund outflow occurred on the Bybit platform. This event resulted in over $14.6 billion being stolen, making it the largest cryptocurrency theft in terms of amount lost in recent years.

On-Chain Tracking Analysis
Following the event, the SlowMist security team immediately issued a security alert and conducted tracking analysis on the stolen assets:

According to the SlowMist security team's analysis, the stolen assets mainly include:
· 401,347 ETH (valued at approximately $10.68 billion)
· 8,000 mETH (valued at approximately $26 million)
· 90,375.5479 stETH (valued at approximately $260 million)
· 15,000 cmETH (valued at approximately $43 million)


Using on-chain tracking and anti-money laundering tool MistTrack, we analyzed the initial hacker address 0x47666Fab8bd0Ac7003bce3f5C3585383F09486E2 and obtained the following information:
The ETH was dispersed in transfers, with the initial hacker address dispersing 400,000 ETH in increments of 10,000 ETH to 40 addresses and continuing to transfer.

Among them, 205 ETH was swapped to BTC via Chainflip and cross-chain transferred to the address bc1qlu4a33zjspefa3tnq566xszcr0fvwz05ewhqfq.

cmETH Destination: 15,000 cmETH was transferred to the address 0x1542368a03ad1f03d96D51B414f4738961Cf4443. It is worth noting that mETH Protocol posted on X, stating that in response to the Bybit security incident, the team promptly suspended cmETH withdrawals, preventing unauthorized withdrawal actions. mETH Protocol successfully reclaimed 15,000 cmETH from the hacker address.

mETH and stETH Transfer: 8,000 mETH and 90,375.5479 stETH were transferred to address 0xA4B2Fd68593B6F34E51cB9eDB66E71c1B4Ab449e. Subsequently, they were exchanged for 98,048 ETH via Uniswap and ParaSwap and then transferred to 0xdd90071d52f20e85c89802e5dc1ec0a7b6475f92. Address 0xdd9 then dispersed the ETH to 9 addresses in 10,000 ETH increments and has not yet made further transfers.

Additionally, tracing back to the address 0x0fa09C3A328792253f8dee7116848723b72a6d2e, which initiated the hack according to the attack methodology analysis section, it was found that the initial funds of that address originated from Binance.

Currently, the initial hacker address 0x47666Fab8bd0Ac7003bce3f5C3585383F09486E2 holds a balance of 1,346 ETH. We will continue to monitor the relevant addresses.

Following the event, SlowMist promptly speculated on the attacker being associated with a North Korean hacker group by analyzing the attacker's acquisition of the Safe multisig and money laundering techniques.

Possible social engineering attack methods that may have been utilized:

Through MistTrack analysis, it was also discovered that the hacker address in this event is linked to the BingX Hacker and Phemex Hacker addresses.


ZachXBT has also confirmed the connection between this attack and the Lazarus Group, a North Korean hacker organization known for conducting international network attacks and cryptocurrency theft. According to ZachXBT's evidence, including test transactions, linked wallets, forensic charts, and time analysis, all demonstrate that the attacker employed common Lazarus Group techniques in multiple operations. Additionally, Arkham stated that all related data has been shared with Bybit to assist the platform in further investigation.

Attack Method Analysis
On the night of the incident at 23:44, Bybit CEO Ben Zhou posted a statement on X, explaining in detail the technical details of the attack:

Through on-chain signature analysis, we discovered some traces:

1. Attacker Deploys Malicious Contract: UTC 2025-02-19 07:15:23, deploys a malicious implementation contract 0xbDd077f651EBe7f7b3cE16fe5F2b025BE2969516.
2. Tampering with Safe Contract Logic: UTC 2025-02-21 14:13:35, through transactions signed by three Owners, replaces the Safe contract with a malicious version: 0x46deef0f52e3a983b67abf4714448a41dd7ffd6d32d32da69d62081c68ad7882. This reveals the address 0x0fa09C3A328792253f8dee7116848723b72a6d2e that initiated the initial attack.
3. Embedding Malicious Logic: Uses DELEGATECALL to write the malicious logic contract to STORAGE 0: 0x96221423681A6d52E184D440a8eFCEbB105C7242.


4. Calling Backdoor Function to Move Funds: The attacker uses the sweepETH and sweepERC20 functions in the contract to transfer all 400,000 ETH and stETH from the cold wallet to an unknown address (total value of approximately $1.5 billion).
From the attack methods, the WazirX hack and the Radiant Capital hack share similarities with this attack, as all three targeted Safe multisig wallets. In the WazirX hack, the attacker similarly deployed a malicious implementation contract in advance, replaced the Safe contract with a malicious implementation contract through transactions signed by three Owners, and used DELEGATECALL to write the malicious logic contract to STORAGE 0 to replace the Safe contract with the malicious implementation contract.


(https://etherscan.io/tx/0x48164d3adbab78c2cb9876f6e17f88e321097fcd14cadd57556866e4ef3e185d)
Regarding the Radiant Capital hack incident, according to official disclosure, the attacker utilized a sophisticated method that caused the signature validator to see a seemingly legitimate transaction on the frontend, similar to the information disclosed in Ben Zhou's tweet.
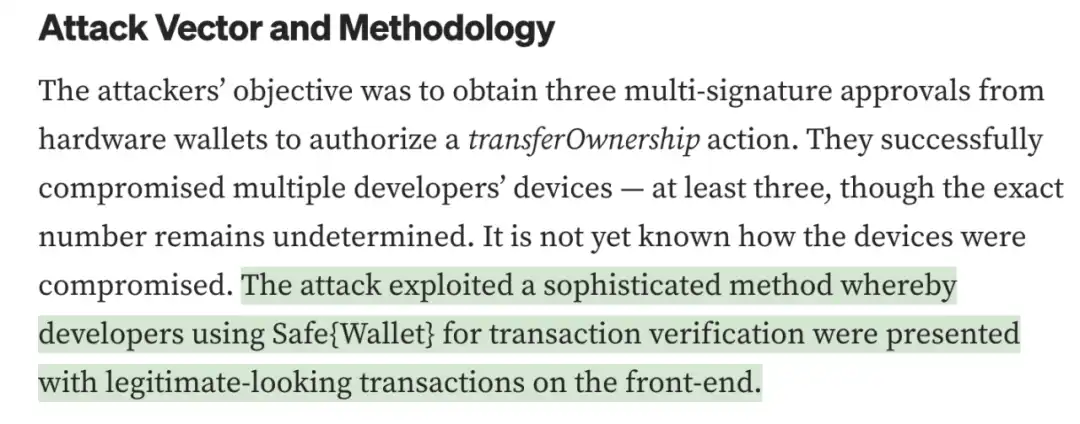
(https://medium.com/@RadiantCapital/radiant-post-mortem-fecd6cd38081)
Furthermore, the permission check method used by the malicious contracts involved in these three incidents was the same, where the owner's address was hardcoded in the contract to check the caller's permissions. The error messages thrown by the permission checks in the Bybit and WazirX hack incidents were also similar.
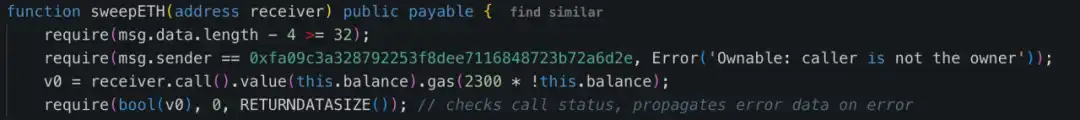
In this incident, the Safe contract was not the issue; the issue lay in the non-contract part where the frontend was tampered with to achieve a deceptive effect. This is not an isolated case. Last year, North Korean hackers used this method to attack several platforms, such as: WazirX losing $230M involving Safe multisig; Radiant Capital losing $50M involving Safe multisig; DMM Bitcoin losing $305M involving Gonco multisig. This attack method is highly engineered and requires extra caution.
According to the official announcement from Bybit:
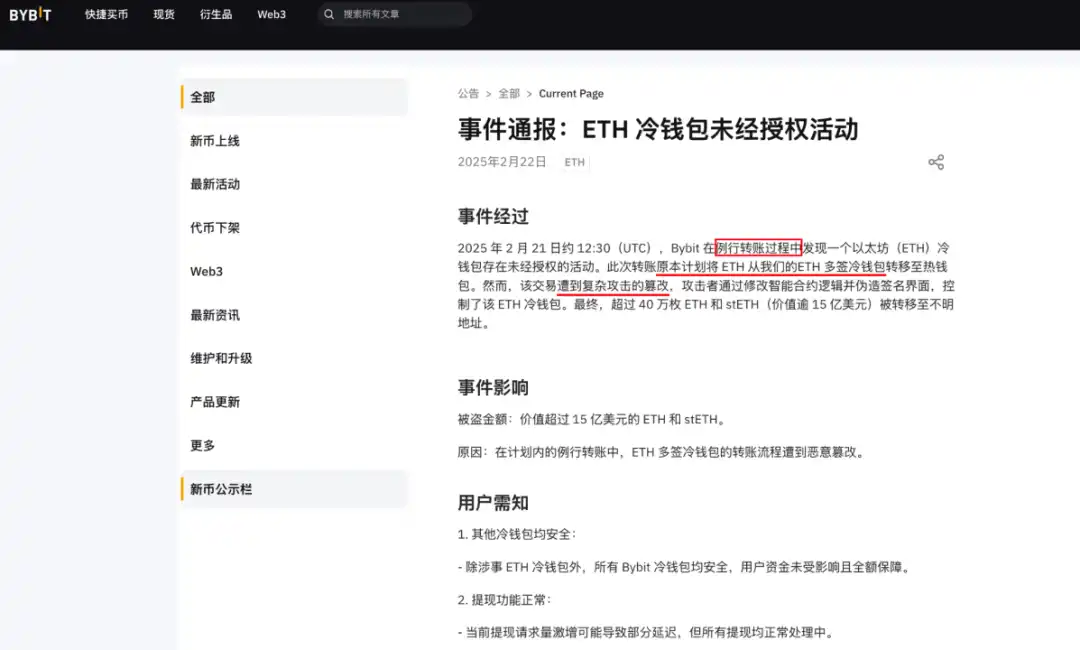
(https://announcements.bybit.com/zh-MY/article/incident-update---eth-cold-wallet-incident-blt292c0454d26e9140)
Combined with Ben Zhou's tweet:
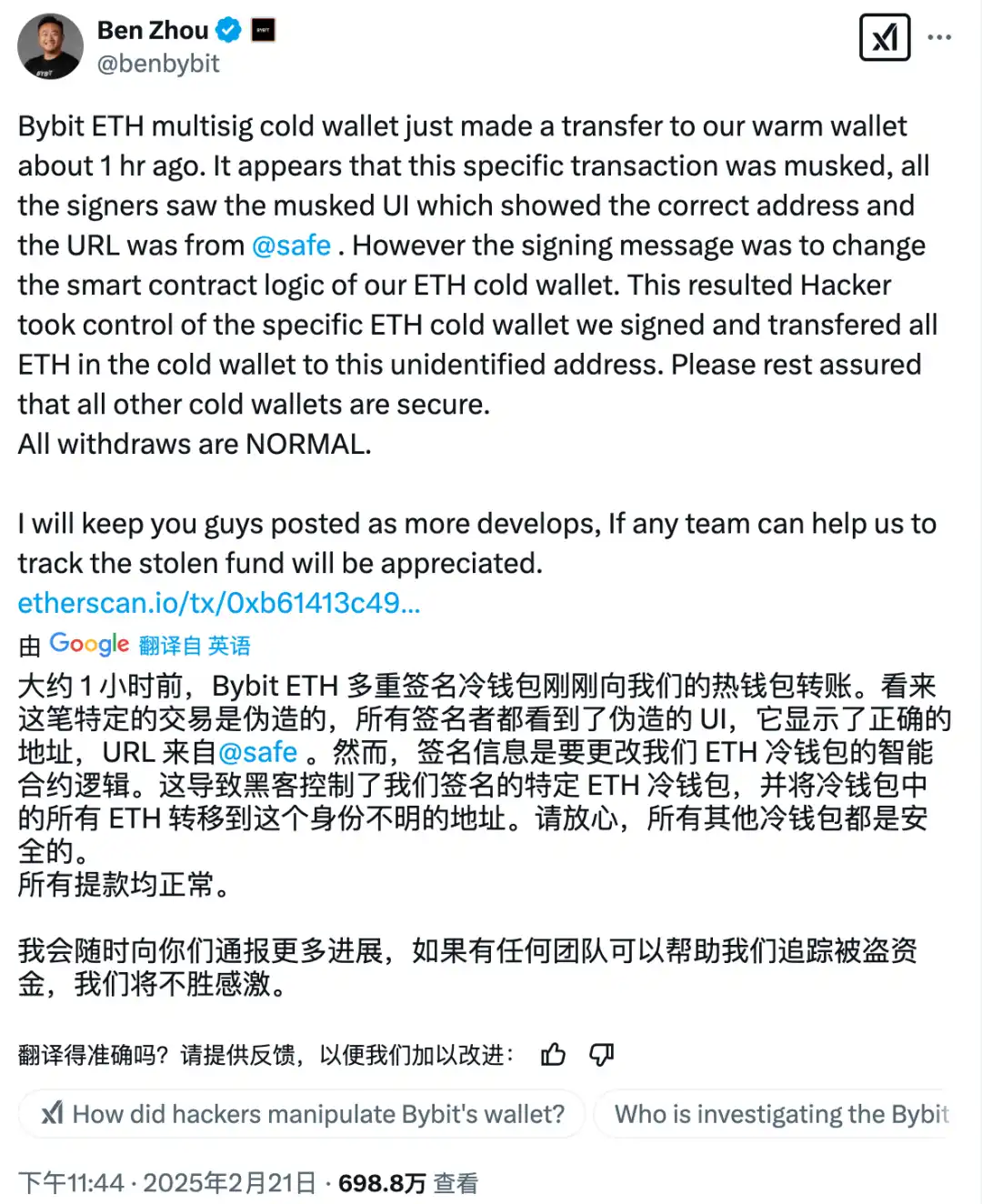
The following questions arise:
1. Routine ETH Transfer
· Did the attacker possibly obtain advance information from Bybit's internal finance team, knowing the timing of the ETH multi-signature cold wallet transfer?
· Did they induce signers through the Safe system to sign a malicious transaction on a forged interface? Was the Safe frontend system hacked and compromised?
2. Safe Contract UI Tampering
· Did signers see the correct address and URL on the Safe interface, but the actual signed transaction data was tampered with?
· The key question is: Who initiated the signature request first? How secure was their device?
With these questions in mind, we look forward to the official disclosure of further investigation results.
Market Impact
After the incident, Bybit promptly released a statement, ensuring that all customer assets are fully reserved and the platform can absorb this loss. User withdrawals are unaffected.
At 10:51 on February 22, 2025, Bybit CEO Ben Zhou announced that deposits and withdrawals are now back to normal:
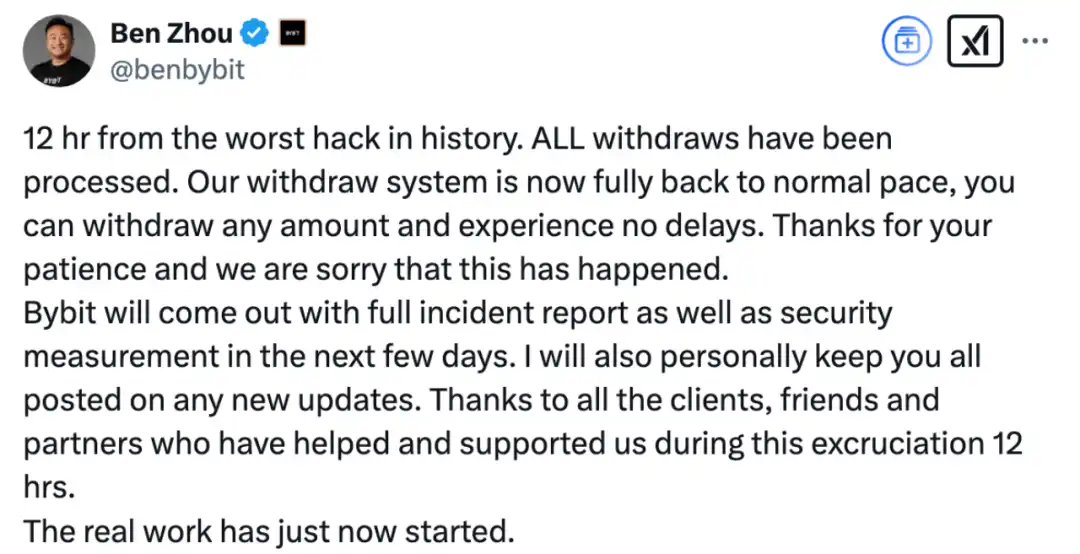
Final Thoughts
This theft incident once again highlights the significant security challenges facing the cryptocurrency industry. With the rapid growth of the crypto industry, hacker groups, especially nation-state hackers like the Lazarus Group, are continuously upgrading their attack methods. This event serves as a wake-up call for cryptocurrency exchanges, urging them to further strengthen their security measures through advanced defense mechanisms such as multi-factor authentication, encrypted wallet management, asset monitoring, and risk assessment to safeguard user assets. For individual users, raising security awareness is equally crucial, and it is recommended to prioritize more secure storage methods like hardware wallets to avoid keeping large amounts of funds on exchanges for an extended period. In this evolving field, only by continuously enhancing technological defenses can we ensure the security of digital assets and promote the industry's healthy development.
欢迎加入律动 BlockBeats 官方社群:
Telegram 订阅群:https://t.me/theblockbeats
Telegram 交流群:https://t.me/BlockBeats_App
Twitter 官方账号:https://twitter.com/BlockBeatsAsia
 Forum
Forum OPRR
OPRR Finance
Finance
 Specials
Specials
 On-chain Eco
On-chain Eco
 Entry
Entry
 Podcasts
Podcasts
 Data
Data

 Summarized by AI
Summarized by AI







