Bybit Event Timeline | The $1.5 Billion Hack Incident was Due to a Safe Vulnerability, Lingering Questions Remain Unanswered
On February 22nd, in the early morning hours, on-chain sleuth Zachxbt detected a suspicious fund outflow incident involving Bybit. On-chain records showed that a multisig address transferred approximately $1.5 billion worth of ETH and used a DEX to swap LSD assets for native ETH. Subsequently, the Bybit CEO issued a statement indicating that a specific ETH cold wallet had been compromised, involving an amount exceeding 500,000 ETH. Approximately 4 hours later, Zachxbt provided evidence confirming that the attack was carried out by the North Korean hacker group Lazarus Group.
On the evening of February 26th, Bybit released a mid-term report on the theft incident, attributing the attack to a vulnerability in the Safe infrastructure. In response, Safe stated that the attack occurred through the intrusion into the Safe{Wallet} developer's device, leading to malicious transactions being disguised as legitimate submissions. External security researchers found no vulnerabilities in the Safe smart contract, frontend, or service source code. Currently, there are still many uncertainties surrounding the theft incident, and BlockBeats will continue to monitor and provide real-time updates. The following is a timeline of the event:
March 4th
SlowMist Cosmos: Most of the nearly $1.5 billion ETH assets stolen from Bybit have flowed into the Bitcoin network
At 11:18, SlowMist Cosmos posted on X platform stating, "The nearly $1.5 billion ETH assets stolen from Bybit, apart from a partial recovery, have mostly left Ethereum, with the vast majority entering the Bitcoin network and undergoing complex mixing operations on Bitcoin, benefiting node operators on the THORChain."
The Bybit hacker has completed the laundering of all 499,000 stolen ETH over 10 days
At 09:04, according to Ashes Monitor, the hacker has successfully laundered all 499,000 ETH (worth $1.39 billion) stolen from Bybit, a process that took 10 days in total.
During this process, the price of ETH dropped by 23% (from $2,780 to the current $2,130). The primary channel used by the hacker for money laundering, THORChain, also saw a volume of $5.9 billion in transactions and $5.5 million in fee income from the hacker's activities.
February 27th
Bybit Hacker Washed 71,000 ETH in the Past 24 Hours, totaling 206,000 ETH
At 9:25, according to on-chain analyst Wu Jinc, in the past 24 hours, the Bybit hacker continued to wash away 71,000 ETH ($170 million). From the afternoon of the 22nd to now, in 4.5 days, 206,000 ETH of the stolen 499,000 ETH has been washed away. An average of 45,000 ETH per day. The hacker's address still holds 292,000 ETH ($685 million).
OKX CEO Star: The Attack on Safe UI has No Impact on OKX
At 6:05, OKX CEO Star posted on X platform, stating, "OKX exchange platform independently developed all hot wallet and cold wallet management systems. In the past 12 years, we have accumulated wallet security and operational practices. The attack on Safe UI this time has no impact on OKX. We will continue to heavily invest in our security infrastructure to ensure the safety of customer funds."
FBI Confirms $1.5 Billion Bybit Theft was North Korean Hackers, Urges Halt to Related Money Laundering Transactions
FBI confirms that the $1.5 billion Bybit theft was carried out by North Korean hackers, and states, "Encourages private sector entities such as RPC node operators, exchange platforms to prevent money laundering transactions associated with the stolen assets' addresses."
CZ: Safe Incident Report Uses Vague Terminology, Multiple Issues Still Unclear
At 0:32, Binance founder CZ posted on social media, saying that he usually does not criticize other industry participants, but the Safe incident report's use of vague language masked the issues. After reading it, there are more questions than answers, and the questions that come to mind for now include:
· What does "Compromise Safe {Wallet} developer's machine" mean? How did they breach this specific machine? Were social engineering, malware involved?
· How did the developer's machine access the "Bybit operational account"? Was some code deployed directly from this developer's machine to prod?
· How did they deceive the Ledger verification step among multiple signers? Was it blind signing? Or signers failed to properly verify?
· Is the $1.4 billion the largest address managed by Safe? Why didn't they target others?
· What can other "self-custody, multi-signature" wallet providers and users learn from this?
Hasu Argues for Safe in Controversy, Wintermute Founder Calls Their Statements Distorted
At 00:00 UTC, Safe investor Hasu took to social media to state that while the recent Bybit hack was due to a Safe frontend issue and not a breach of Bybit's infrastructure, Bybit's infrastructure was also inadequate to detect such a simple hack. When transferring funds exceeding $1 billion, there is no reason not to verify the integrity of messages on a second offline machine. Blaming SAFE here instead of Bybit would be a complete misreading of the lessons to be learned.
In response, Wintermute founder wishfulcynic.eth commented that Hasu's statements were somewhat misleading and distorted (gaslighting).
Hasu countered in a series of replies, stating that it is difficult to assess whether Safe was at fault in the incident (not because he is a Safe investor). Safe provided a solution through a centralized frontend but should never rely on it entirely. He believes Safe's biggest issue was not collaborating with large fund clients for security education. The compromise of Safe developer devices was also a concern, but learning from it is more crucial.
February 26
Safe: Bybit Hack Due to Compromise of Developer Device, No Vulnerabilities in Contracts and Frontend Code
At 23:16 UTC, Safe posted on social media that the attack on Bybit was carried out by compromising the Safe{Wallet} developer's device, leading to malicious transactions disguised as legitimate trades. External security reviews did not uncover any vulnerabilities in Safe smart contracts or frontend and service source code.
The Safe{Wallet} frontend remains operational and has implemented additional security measures. However, users are advised to exercise extra caution and remain vigilant when signing transactions.
Bybit: $1.5 Billion Theft Due to Safe Infrastructure Vulnerability
At 23:00 UTC, according to a mid-event report released by Bybit (provided by Sygnia) regarding the $1.5 billion theft incident, the theft was due to a Safe infrastructure vulnerability, with no anomalies in Bybit-related infrastructure.
SlowMist: Bybit Could Have Avoided $1.5 Billion Asset Theft If Upgraded to Safe Contract 1.3.0 or Higher with Proper Guard Mechanism
At 16:29, SlowMist revealed that on February 21, 2025, Bybit's on-chain multisig wallet was breached through a targeted attack, resulting in the stealthy loss of nearly $1.5 billion in assets through a transaction with a "legitimate signature." Subsequent on-chain analysis showed that the attacker, through sophisticated social engineering, gained multisig permissions, exploited the Safe contract's delegatecall functionality to implant malicious logic, and ultimately bypassed the multisig verification mechanism to transfer the funds to an anonymous address. "Multisig" does not equal "absolute security," and even robust security mechanisms like the Safe multisig wallet are still at risk of being breached if additional protective measures are lacking.
Bybit was using version 1.1.1 (<1.3.0) of the Safe contract, which means they were unable to utilize the Guard mechanism, a key security feature. If Bybit upgrades to Safe contract version 1.3.0 or higher and implements an appropriate Guard mechanism, such as specifying a unique whitelisted address to receive funds and enforcing strict contract function ACL validation, they may have been able to prevent this loss. While this is just a hypothesis, it provides an important insight for future asset security management.
Bybit Hacker Cleansed 45,900 ETH in the Past 24 Hours, Accumulating a Total of 135,000 ETH
At 9:35, according to EmberCN's monitoring, the Bybit hacker cleansed 45,900 ETH ($113 million) in the past 24 hours. They have already cleansed a total of 135,000 ETH ($335 million), close to one-third of the stolen amount. The Bybit hacker address still holds 363,900 ETH ($900 million). At the current rate, it would only take another 8 to 10 days to completely cleanse and transfer out all the stolen funds.
February 25
SlowMist Cosine: Bybit's Bounty Design Could Lead to Entities with Less than 5% Laundering Fee Defecting
At 23:10, SlowMist Cosine posted on X platform that Bybit launched a bounty website targeting the Lazarus Group, with the stolen funds from Bybit valued at approximately $1.5 billion a few days ago. A 10% recovery bounty with 5% going to the entity successfully freezing the funds and 5% to contributors aiding in fund tracking. If a particular entity cannot receive a laundering fee above 5%, they could easily defect.
Bybit Launches Lazarus Hacker Organization Bounty Website, 5% Reward for Fund Recovery Contributors
At 10:40 PM, Bybit CEO Ben Zhou posted on social media, stating, "The Lazarus Hacker Organization bounty website has been launched, displaying transparent data on Lazarus money laundering activities."
The total bounty for fund recovery is 10%, and if all funds are recovered, the total bounty could be as high as $140 million. The specific allocation is as follows: 5% to the entity that successfully freezes the funds, 5% to contributors who help track the funds.
Bybit Hacker Has Laundered 89,500 ETH, Expected to Complete Money Laundering Within Two Weeks
At 9:09 AM, according to EmberSec monitoring, the Bybit hacker has already laundered 89,500 ETH (approximately $224 million) in the past 2.5 days, which accounts for 18% of the total ETH stolen (499,000 ETH). At this rate, the hacker is on track to exchange the remaining 410,000 ETH for other assets (BTC/DAI, etc.) in the next half month. The hacker's cross-chain asset exchange is currently mainly done through THORChain.
February 24
Bybit Hacker is Using Multiple DEXs to Sell ETH for DAI
At 6:12 PM, according to lmk.fun (formerly Scopescan) monitoring, the Bybit hacker is using multiple DEXs to convert ETH into DAI. The hacker has sent $3.64 million worth of ETH to another address and is now transferring out DAI.
Bybit CEO: Back to 1:1 Solvency, About to Launch Stolen Fund Flow Website
Around 4 PM, Bybit CEO Ben Zhou stated in a community AMA that they have received the latest asset proof audit report, which will be updated on the official website synchronously. Bybit has returned to 1:1 solvency, and in the past 24 hours, Bybit's fund inflow ranks first among global CEXs.
Bybit will launch a stolen fund flow website and synchronize recovery progress and other data. Users providing valid clues can receive a reward. Bybit's new coin disclosure board regularly publishes the performance and financial reports of listed projects in 5 dimensions: core financial data, token metrics, on-chain activities and network health, governance and community, as well as risk disclosure and future roadmap.
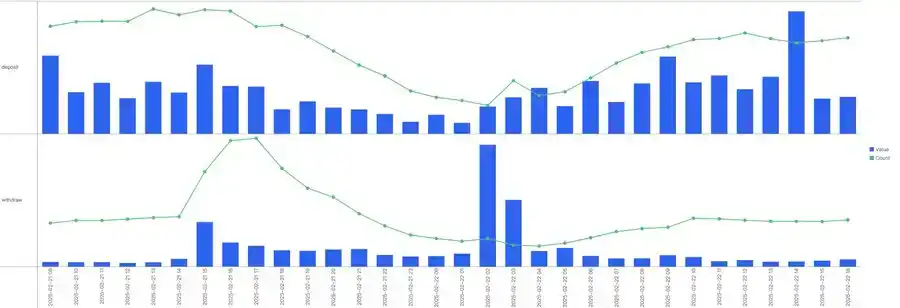
Bybit: ETH Reserve Close to 100%, Deposits and Withdrawals Resumed Normal Operations
At 15:39, Bybit released a latest announcement stating, "Our ETH reserve is close to 100%, and deposits and withdrawals have resumed normal operations. Throughout the entire process, the crypto community, our partners, and users have shown unwavering support—thank you all. We are clear on the destination of the funds and are committed to turning this experience into an opportunity to strengthen the ecosystem."
Bybit: 15,000 cmETH Recovered Successfully by mETH Protocol Team
At 14:17, Bybit's official statement indicated that the mETH Protocol team played a crucial role in the recent security incident. Through swift action and effective coordination, the mETH Protocol team successfully recovered 15,000 cmETH tokens, valued at around $43 million.
Bybit CEO: Bybit Has Fully Recovered ETH Shortfall
At 11:26, Bybit CEO Ben Zhou posted an update stating, "Bybit has fully recovered the ETH shortfall, and a brand-new Proof of Reserves (POR) report is set to be released soon. Stay tuned."
Bybit Acquired Approximately 446.87k ETH Through Loans, Whale Deposits, and Purchases
At 10:35, according to lookonchain monitoring, since the hack, Bybit has acquired approximately 446,870 ETH (~$1.23 billion) through loans, whale deposits, and purchases. Bybit is close to recovering the losses.
eXch Denies Assisting Lazarus Group in Money Laundering
In a post on the Bitcointalk forum, eXch stated, "The platform does not support Lazarus money laundering. The opposing view is merely a perspective of some individuals who wish to see the fungibility and on-chain privacy of decentralized currency disappear—a sentiment long harbored by those averse to decentralized cryptocurrencies."
eXch acknowledges that a small portion of the funds from the Bybit hack made their way to its platform address but describes the transaction as "an isolated case." The eXch team pledges to donate the funds to "various open-source initiatives dedicated to privacy and security within and outside the crypto space."
Security Update: Bybit Hacker Laundering Method Stabilizes, Primarily Using Thorchain to Move Assets into BTC
At 9:32 AM, BeosinTrace reported that at 08:58:23 AM UTC+8 today, they tracked the Bybit hacker once again transferring assets. The hacker's selling pattern has stabilized, mainly moving assets into the BTC chain through Thorchain and exchanging them for DAI using OKX DEX. The exchanged DAI will flow into eXch.
February 23
Bybit: Successfully Freezes $42.89 Million of Stolen Funds, Thanks to Multi-Party Coordination Efforts
At 11:41 PM, the Bybit team announced that they had successfully frozen $42.89 million of stolen funds within a day thanks to multi-party coordination efforts. The assisting institutions included Tether, THORChain, ChangeNOW, FixedFloat, Avalanche Ecosystem, CoinEx, Bitget, Circle, among others.
pump.fun Has Removed Lazarus Group-Related Meme Coins from the Front End
Around 10:52 PM, pump.fun removed Lazarus Group-related Meme coins from the front end related to the Bybit incident attacker, the North Korean hacker group Lazarus Group.
ZachXBT: Entity Laundering Bybit Hack Funds through Issuing and Trading Meme Coins on pump.fun
At 9:05 PM, blockchain sleuth ZachXBT posted in their personal channel revealing that they found an entity laundering Bybit stolen funds through issuing and trading meme coins on pump.fun.
On February 22, the attacker received $1.08 million in funds from the Bybit hack at address "0x363908...d7d1" and then cross-chain transferred USDC to the Solana chain. Subsequently, all USDC on the Solana chain was cross-chain transferred to two addresses on the BSC chain. The two BSC addresses programmatically dispersed the USDC to over 30 addresses before consolidating. Then, 10.6k USDC was split among 10 BSC addresses and cross-chained back to 10 Solana addresses. The launderer converted the received SOL into meme coins.
15 hours ago, on-chain sleuth ZachXBT publicly revealed over 920 addresses that received funds from the Bybit hacker and found that a money launderer had issued meme coins through the pump.fun platform for the North Korean hacker group Lazarus Group. For security reasons, specific wallet addresses are not being disclosed at this time, and multiple analysis tools have been requested to take down related interfaces.
Bybit Raised 254,830 ETH, Approximately $6.93 Billion, Within 48 Hours of the Hack
At 22:04, according to the latest data update from Spotonchain, Bybit raised 254,830 ETH ($6.93 billion) within 48 hours of the hack, including:
132,178 ETH ($3.67 billion), potentially acquired through OTC trades with Galaxy Digital, FalconX, and Wintermute; 122,652 ETH ($3.26 billion), sourced from loans from exchanges/institutions such as Bitget, MEXC, Binance, and DWF Labs (which may also involve personal borrowing behavior by some whales).
Additionally, the hacker has cross-chain exchanged 40,944 ETH ($1.15 billion) into BTC and other assets through Chainflip, THORChain, LiFi, DLN, and eXch. Currently, the hacker still holds 458,451 ETH ($12.9 billion)—approximately 91.7% of the stolen 499,395 ETH ($14 billion).
Bybit: Fraudsters Impersonating Bybit Employees, Community Cautioned
At 20:53, Bybit's official announcement stated that scammers are impersonating Bybit employees. Users are advised to remain vigilant, always verify official sources, and report any suspicious activity. Bybit will not ask for personal information, deposits, or passwords.
Bybit Hacker Has Cross-Chain Exchanged 37,900 ETH, with 461,491 ETH Remaining
At 20:22, according to EmberCN monitoring, the Bybit hacker has cross-chain exchanged 37,900 ETH ($1.06 billion) into other assets (such as BTC) using numerous addresses and platforms like Chainflip, THORChain, LiFi, DLN, eXch. The laundering of funds has taken 30 hours from yesterday until now.
The Bybit hacker address currently holds 461,491 ETH (1.29 billion USD) remaining, with a total of 499,395 ETH (1.4 billion USD) stolen from Bybit.
Bybit: Deposits and Withdrawals Fully Restored to Normal
At 16:55, Bybit's official statement confirmed that deposits and withdrawals on Bybit have been fully restored to normal levels, as evidenced by on-chain data.
Bybit CEO Responds to eXch's Refusal to Intercept Request: "Hoping eXch Reconsiders, This Is Not Just About Helping Bybit"
At 12:32, Bybit CEO Ben Zhou, on the X platform, stated, "At this moment, it's not about Bybit or any entity, but rather about how we as an industry treat hackers in general. I sincerely hope eXch can reconsider and help us prevent funds from flowing out through them. We have also received assistance from Interpool and international regulatory agencies, and helping to stop these funds is not just about helping Bybit."
SlowMist: Mixing Platform eXch Has Helped Hacker Convert ETH to BTC, XMR, Suggests CEX Enhance Risk Control Level
At 11:27, SlowMist's SlowMist stated that given a significant amount of ETH has already been laundered through eXch, converted to BTC, XMR, etc., all platforms should enhance their risk control level for funds originating from eXch.
Ethereum Core Developer: Rollback Nearly Impossible to Achieve, May Trigger Irreparable Cascade
On February 23, regarding the February 21 Bybit exchange hack resulting in a $1.5 billion loss, Ethereum Core Developer Tim Beiko stated that despite some in the crypto industry calling for the Ethereum network to be restored to a pre-attack state, from a technical perspective, this is almost impossible to achieve. Beiko emphasized that unlike the 2016 TheDAO hack, this attack did not violate Ethereum protocol rules, and a rollback would cause widespread and irreparable cascades, potentially leading to more destructive consequences than the hacker's loss. Additionally, a rollback would reverse all settled on-chain transactions, unable to undo off-chain transactions.
Other industry figures echoed similar sentiments. Ethereum educator Anthony Sassano pointed out that the current complexity of the Ethereum ecosystem makes a simple rollback of infrastructure unworkable. Yuga Labs' VP of Blockchain also cautioned that the cost of a rollback could far exceed $1.5 billion.
Bybit CEO Responds to Whether to Support Ethereum Rollback to Pre-Hack State: Should Be Decided by Community Vote
Regarding whether to support an Ethereum rollback to the pre-hack state, Bybit CEO Ben Zhou expressed in a previous Space session: "I'm not sure if it's one man's decision. Based on the spirit of blockchain, maybe it should be a voting process to see what the community's want, but I am not sure."
February 22
Bybit Launches "Bounty Recovery Program," Rewarding 10% of Stolen Funds
At 23:32, according to an official announcement, Bybit officially launched the "Bounty Recovery Program," calling on global cybersecurity and crypto analysis elites to jointly track down the perpetrators of the largest crypto theft in history.
Contributors who successfully recover funds will receive a 10% reward, with the total bounty amount calculated based on the verifiable recovery amount of the stolen ETH, valued at over $1.4 billion at the time of the event. If all funds are recovered, the total bounty amount could reach up to $140 million.
Bybit CEO Ben Zhou stated that within 24 hours of the incident, the platform had received strong support from top industry professionals and organizations. Through the "Bounty Recovery Program," we aim to formally reward community members who provide us with expertise, experience, and support. We will not stop here. Those interested in participating can contact the platform at bounty_program@bybit.com.
Bybit CEO: Agrees with CZ's View, Will Immediately Halt All Withdrawals if Internal Systems Are Breached
At 21:17, Bybit CEO Ben Zhou posted, "I agree with CZ's view that if this hack was through penetrating our internal systems (e.g., part of the withdrawal system) or breaching the hot wallet, we will immediately suspend all withdrawals until the root cause is found.
However, in yesterday's incident, it was our ETH cold wallet that was breached (we use Safe), which is unrelated to any of our internal systems. Therefore, I could decisively decide to have all Bybit withdrawals and system functions operate as usual."
In last night's crisis, Binance and CZ, along with many partners and industry leaders, proactively offered help, for which we are deeply grateful and incredibly warmed by the support received. This event was a major blow to Bybit, but the entire industry has shown the power of unity. I believe that from now on, everything will only move in a better direction."
CZ: The suggestion for ByBit to pause withdrawals was based on self-experience and observation, with the principle always standing on the safer side
At 20:19, CZ wrote, "Recent events (including ByBit, Phemex, WazirX, etc.) have shown a pattern: hackers are able to steal a large amount of cryptocurrency from multi-signature 'cold storage' solutions. In the latest ByBit case, the hacker was able to make the frontend user interface display a legitimate transaction, while the actual signing was for another transaction. Although I am less familiar with other cases, based on the limited information, they seem to have similar characteristics."
Some questioned my suggestion to immediately pause all withdrawals in the event of a security incident (I sent this tweet while on the airport shuttle). My intention was based on self-experience and observation, sharing a practical response. Of course, there is no absolute right or wrong. My principle has always been to err on the side of safety. After a security incident, all operations should be paused immediately, ensuring a full understanding of the attack method, identifying how the hacker penetrated the system, which devices were affected, triple-checking security before resuming operations.
Of course, pausing withdrawals may cause greater panic. In 2019, after experiencing a $40 million hack, we paused withdrawals for a week. But when we resumed withdrawals (and deposits), the deposit volume was actually higher than the withdrawal volume. I am not saying this method is better; each situation is different and requires judgment. The purpose of my tweet was to share a potentially effective method and express support in a timely manner."
"I believe Ben made the best decision based on the information he had. Ben maintained transparent communication and a calm attitude during this crisis, in sharp contrast to less transparent CEOs such as WazirX and FTX. It is important to emphasize that the nature of these cases is different. FTX is a fraud case, and the WazirX case is still in litigation, so I cannot comment."
Bybit CEO: Bitget was the first helping CEX, with no interest demands
During the 19:00 Space event, Bybit's CEO stated that Bitget was the first helping CEX, with no interest demands. Additionally, MEXC and Gate.io also provided assistance.
Bitget CEO Gracy stated in Space that she actively communicated with Bybit CEO BEN and proactively offered help, providing short-term liquidity without requiring any collateral, interest, or commitment. Bybit could return the liquidity when no longer needed. The current understanding is that Bybit's liquidity has been improved and no further support is needed.
mETH Protocol: cmETH Withdrawals Resumed, User Funds Unaffected
At 5:54 PM, the liquidity staking/restaking protocol mETH Protocol announced that cmETH withdrawals have resumed, with user funds safe and fully supported. A detailed post-mortem analysis report will be released soon, outlining the events and all measures taken.
Prior to this, mETH Protocol had announced the suspension of cmETH withdrawals after learning about a recent security incident involving certain mETH and cmETH transactions on Bybit, while deposits and staking services continued as usual.
5 Institutions/Individuals Have Provided Bybit with Supportive Loans of 120,000 ETH
At 5:50 PM, according to EmberCN monitoring, a total of 5 institutions/individuals have provided supportive loans to Bybit, totaling 120,000 ETH ($320.97M). They are:
· Bitget: 40,000 ETH ($105.96M);
· Whale/Institution withdrawing from Binance: 11,800 ETH ($31.02M);
· MEXC: 12,652 stETH ($33.75M);
· Binance or another Whale/Institution withdrawing from Binance: 36,000 ETH ($96.54M);
· Address 0x327...45b: 20,000 ETH ($53.7M).
Chainflip: Strengthening ETH Custody Level Filtering Mechanism to Reject Suspicious Deposits
At 4:52 PM, the cross-chain bridge Chainflip updated on the latest developments of the Bybit hack, stating, "We have noticed that the hacker attempted to convert the stolen Bybit funds to BTC via Chainflip. Currently, we have shut down some frontend services to prevent fund movement. However, as the protocol is fully decentralized with 150 nodes, we cannot completely shut down the entire system."
As a longer-term solution, we are strengthening the ETH custody level filtering mechanism to reject suspicious deposits via the broker API. Currently, this mechanism is already in place for BTC, and we just need to complete the implementation for ETH.
Chainflip Response to Bybit CEO: As a Decentralized Protocol, We Cannot Fully Stop, Freeze, or Redirect Any Funds
At 16:33, the cross-chain bridge Chainflip responded to the Bybit CEO's freeze request stating, "We have tried our best to handle the current situation, but as a decentralized protocol, we cannot fully stop, freeze, or redirect any funds. However, we have currently shut down some frontend services to prevent fund movement."
ZachXBT: Bybit Hacker Begins Mixing Funds with Phemex Hack Funds
At 16:09, on-chain sleuth ZachXBT posted on social media stating that the Lazarus Group had just merged a portion of the Bybit hack attack funds with the Phemex hack attack funds directly on-chain, mixing the funds from the initial theft addresses of both incidents.
ZachXBT: Monitoring Bybit Hacker Moving Assets and Laundering Through a Mixer
On-chain sleuth ZachXBT posted in the official channel indicating that they observed the Lazarus Group moving 5000 ETH from the Bybit hacker address to a new address, starting to launder through an eXch (centralized mixer), and transferring the funds into the Bitcoin network via Chainflip.
Bybit CEO: Hacker Detected Trying to Move Assets Through Chainflip, Will Soon Launch Bounty Program for the Cross-Chain Bridge
At 15:21, Bybit CEO Ben Zhou posted on social media that they detected the hacker attempting to move assets to the BTC network via Chainflip. They hope the cross-chain bridge project can assist Bybit in preventing and stopping further asset movement to other chains. Bybit will soon release a bounty program for anyone who helps in blocking or tracing funds that lead to fund recovery.
Bybit's Funds Inflow Exceeded $4 Billion in the Past 12 Hours, Covering the Entire Stolen Funds Gap
According to SoSoValue statistics and the latest monitoring data from the on-chain security team TenArmor, the Bybit trading platform has received a total inflow of funds exceeding $4 billion in the past 12 hours, including 63,168.08 ETH, $3.15 billion USDT, $173 million USDC, and $525 million CUSD.
According to the comparison of fund flow data, the current fund inflow has fully covered the fund gap caused by yesterday's hacker attack. At the same time, all services of the Bybit trading platform, including the withdrawal function, have been restored to normal.
SlowMist Cosmos: In the case where the attack reason is unknown, CZ's proposed withdrawal suspension is also correct
At 14:29, SlowMist founder Cosmos posted on social media, stating that from a security perspective, it is right to suggest an emergency halt to the wallet system when the reason is unknown. Bybit's response to this theft was extremely quick and the problem was identified very quickly. SlowMist, along with some security teams, immediately engaged in communication and quickly identified the problem and speculated on the hacker's profile. Bybit was well-prepared and there was no problem with timely resuming withdrawals.
Cosmos explained that he believes both CZ's previous suggestion and Bybit's final resolution were correct. At present, many industry insiders are squabbling over this controversy but have forgotten that the common enemy should be the North Korean hackers.
Du Jun: Will transfer 10,000 ETH to Bybit and will not withdraw for one month
At 12:32, ABCDE co-founder Du Jun posted on social media, stating that he will personally transfer 10,000 ETH to Bybit today and will not withdraw for one month.
WSJ: CertiK confirms Bybit incident as the largest theft in crypto history
The Wall Street Journal cited the opinion of Web3.0 security firm CertiK, stating that the recent Bybit incident is the largest single theft event in crypto history, with the stolen assets from this hacker attack valued at over $1.4 billion.
Following the incident, Bybit announced that it has reported the case to the relevant authorities. Bybit's CEO Ben Zhou stated that all of Bybit's functions and products are operating normally, the exchange has the ability to pay, and will fully compensate customer losses. As of now, all withdrawal requests at Bybit have been processed, and the withdrawal system has resumed normal speed.
SlowMist Cosmos: Safe Frontend was tampered with and counterfeited to achieve a deceptive effect; North Korean hackers have conducted similar operations multiple times
At 11:40, SlowMist founder Cosmos posted on social media, stating that the Safe contract is not the issue; the issue lies in the non-contract part, where the frontend was tampered with and counterfeited to achieve a deceptive effect. This is not an isolated case; North Korean hackers successfully used this method several times last year, such as in the WazirX incident (stolen $230 million, Safe multisig), Radiant Capital incident (stolen $50 million, Safe multisig), DMM (stolen $305 million, Gonco multisig). This attack method is mature and engineered. Other institutions also need to pay more attention, as multisig may have such attack vectors beyond Safe.
Bybit Hacker's ETH Holdings Surpass Fidelity and Vitalik, Becoming the 14th Largest Holder Globally
Coinbase executive Conor Grogan stated on social media that the Bybit hacker (suspected to be from North Korea) has become the 14th largest ETH holder globally, with holdings representing approximately 0.42% of the total Ethereum token supply. This amount has surpassed the holdings of Fidelity Investment Company, Ethereum co-founder Vitalik Buterin, and is more than twice that of the Ethereum Foundation's ETH holdings.
Bybit CEO: Withdrawal System Now Fully Restored, Will Release Full Incident Report
At 10:51 AM, Bybit CEO Ben Zhou announced that it has been 12 hours since the worst hack in history. All withdrawals have been processed. The Bybit withdrawal system is now fully restored, allowing users to withdraw any amount without any delays. Thanks to users for their patience, Bybit apologizes for the occurrence. Bybit will release a full incident report and security measures in the coming days.
Bybit Hacker's 15,000 cmETH Unstaking Request Rejected, Could Potentially Be Successfully Intercepted
At 9:15 AM, according to on-chain data analyst Yu Jin Monitoring, an hour ago, the Bybit hacker's unstaking request of 15,000 cmETH was rejected by the cmETH withdrawal contract. Subsequently, the hacker granted cmETH trading authorization on DODO but did not proceed with any further transactions, possibly due to the shallow liquidity pool of cmETH.
This 15,000 cmETH could potentially have been intercepted. Apart from this 15,000 cmETH, the amount of ETH stolen from Bybit is 499,000 coins (approximately $1.37 billion) distributed across 51 addresses by the hacker.
Safe: No Security Vulnerabilities Found After Comprehensive Audit, No Other Safe Addresses Affected
At 9:08 AM, Safe responded on social media to the issue of "ByBit displaying what appears to be the correct transaction information but on-chain executing a malicious transaction with all valid signatures" with the following:
· No Codebase Leak Found: A thorough examination of the Safe codebase revealed no evidence of leaks or modifications.
· No Malicious Dependencies Found: There is no evidence to suggest that malicious dependencies in the Safe codebase would impact transaction flow (i.e., a supply chain attack)
· No Unauthorized Access to Infrastructure Detected in Logs
· No Other Safe Addresses Affected
Safe has indicated that it has temporarily paused Safe{Wallet} functionality to ensure users have absolute confidence in the security of the Safe platform. While the investigation has shown no evidence of a breach to the Safe{Wallet} frontend itself, we are conducting a more thorough review.
Bybit CEO: 99.99% of Withdrawal Requests Processed
At 8:52, Bybit CEO Ben Zhou posted on social media stating that since the hack incident (10 hours ago), Bybit has experienced the largest number of withdrawals we have ever seen, with over 350,000 withdrawal requests in total, approximately 2,100 withdrawal requests are pending processing. 99.994% of withdrawals have been completed so far. The entire team stayed up all night, handling and addressing customer questions and concerns.
Bitget Transfers 40,000 ETH to Bybit 5 Hours Ago to Alleviate Withdrawal Pressure
Around 9:00, according to on-chain data analyst Yu Jin's monitoring, 5 hours ago, Bitget loaned 40,000 ETH to Bybit to get through the withdrawal craze following the ETH theft. These ETH were directly transferred from Bitget to Bybit's cold wallet address.
At 7:27, Bybit CEO Ben Zhou responded to the news that "Binance and Bitget have cumulatively deposited over 50,000 ETH into Bybit's cold wallets" on social media, thanking Bitget for extending a helping hand at this moment. Bybit is still in communication with Binance and several other partners, and the funds described in the news are unrelated to the official Binance.
Bybit: Collaborating Extensively with On-Chain Analytics Firms to Limit Hacker's ETH Dump
At 5:07, Bybit's official social media post stated that it has reported the theft to the relevant authorities. Once any further information is obtained, updates will be immediately provided. Bybit has also engaged in rapid and extensive collaboration with on-chain analytics providers to identify all involved addresses. These actions will mitigate and combat the bad actors' ability to dispose and sell ETH through legitimate markets, thereby narrowing the available disposal channels.
North Korean Lazarus Group Accused of Orchestrating Bybit Hack
At 4:21 AM, Arkham posted on Platform X stating that ZachXBT submitted evidence at 19:09 UTC proving that the North Korean Lazarus Group orchestrated the attack. The evidence included test transaction analysis, related wallet connections, and forensic charts. The report has been submitted to the Bybit team for investigation assistance.
Bybit CEO: Issue Found with Multi-Signature Transfers but Overlooked, Peak Withdrawal Pressure Now Passed
At 1:29 AM, Bybit CEO Ben Zhou shared during a livestream that "he was the last one to sign during the multi-signature transfer, using the ledger device, there was an issue during signing but it was overlooked, the destination address was not displayed during signing. Currently, there are 4000 withdrawal transactions in pending status."
Ben Zhou reiterated during the livestream that Bybit's treasury can cover the loss of 400,000 Ether. "We have processed 70% of withdrawals, the peak withdrawal pressure has passed, large withdrawals are undergoing routine security checks, and over the next few hours, we are still processing the remaining withdrawals. All customer withdrawals will be processed."
Ben Zhou also mentioned that they are considering obtaining a bridge loan from a partner to cover the stolen funds. "We will not purchase Ether, considering obtaining a bridge loan from a partner to cover the stolen funds, 80% of it has been secured."
Safe Security Team Collaborating with Bybit, No Evidence of Safe Frontend Breach Yet
At 12:47 AM, the Safe Security Team stated in a post that they are closely collaborating with Bybit for ongoing investigations. Currently, no evidence of an official Safe frontend breach has been found. However, out of caution, Safe{Wallet} has temporarily suspended some functions. User security is our top priority, and we will provide more updates as soon as possible.
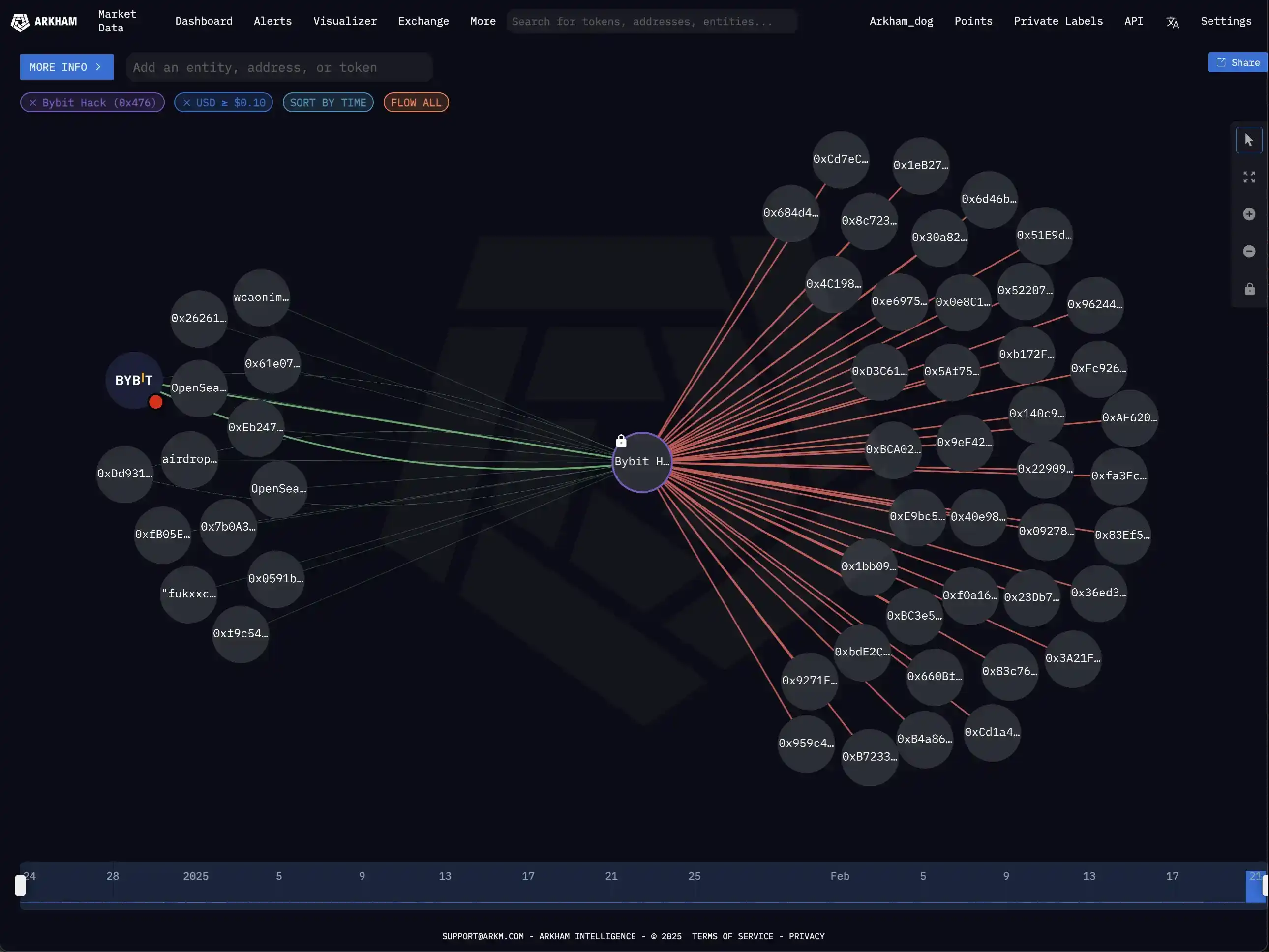
Bybit Hacker Has Transferred 490,000 ETH to 49 Addresses, with 15,000 cmETH Still Pending Unstaking
At 12:45 AM, according to EmberCN monitoring, Bybit's ETH multi-signature cold wallet was hacked for 514,000 ETH, worth $14.29 billion. The hacker has already dispersed 490,000 ETH to 49 addresses (10,000 ETH per address). "Additionally, there are 15,000 cmETH currently being unstaked by the hacker (with an 8-hour waiting period, it is unknown if this can be intercepted)."
SlowMist Discloses Bybit Hacker Incident Details
At 00:36, SlowMist published a post disclosing the details of the Bybit hacker incident:
· The malicious implementation contract was deployed at UTC 2025-02-19 7:15:23
0xbDd077f651EBe7f7b3cE16fe5F2b025BE2969516
· The attacker at UTC 2025-02-21 14:13:35 used three owner signatures to execute a transaction replacing the Safe implementation contract with the malicious contract
0x46deef0f52e3a983b67abf4714448a41dd7ffd6d32d32da69d62081c68ad7882
· The malicious upgrade logic was embedded in STORAGE[0x0] via DELEGATECALL
0x96221423681A6d52E184D440a8eFCEbB105C7242
· The attacker used the backdoor functions sweepETH and sweepERC20 in the malicious contract to drain the hot wallet.
He Yi, CZ, Justin Sun Successively Voice Support for Bybit, Expressing Willingness to Provide Assistance at Any Time
At 00:29, Binance co-founder He Yi responded to the Bybit hack on social media, stating, "We are here when you need, ready to provide help at any time."
At 00:34, Binance founder CZ responded to the Bybit hack on social media, saying, "This is not an easy situation to deal with. I suggest temporarily suspending all withdrawals as a standard security precaution. If needed, I am willing to provide any assistance. Good luck!"
At 00:39, Huobi HTX global advisor and TRON founder Justin Sun responded to the Bybit hack on social media, saying, "We have been closely monitoring the Bybit incident and will make every effort to assist our partners in tracking related funds and providing all the support we can within our capabilities."
Defillama Founder: Net Withdrawal Outflow After Bybit Hack Incident Reaches $700 Million
At 00:23, Defillama founder 0xngmi shared on social media, "So far, after the Bybit hack incident, the net outflow amount due to user withdrawals has reached $700 million."
Bybit Hack: 514,723 ETH Stolen, Including Various Derivative ETH
According to OnchainLens monitoring, the Bybit hack fund outflow is as follows:
· 401,347 ETH, valued at $1.12 billion;
· 90,376 stETH, valued at $253.16 million;
· 15,000 cmETH, valued at $41.13 million;
· 8,000 mETH, valued at $23 million.
The total amount of stolen native ETH and various derivative ETH is 514,723.
Bybit CEO: Will Soon Host Livestream to Answer All Questions
At 0:20, Bybit CEO Ben Zhou posted an update on Platform X stating, "I will soon start a livestream to answer all questions!! Please stay tuned."
Ethena: Bybit's Hedge Position PNL Is Less Than $30 Million, USDe Spot Assets Held Outside of CEX
At 0:16, Ethena Labs stated, "We are aware of the current situation developing with Bybit and will continue to monitor the latest updates. Reminder: all USDe-supporting spot assets are held in custody solutions outside of exchanges, including Bybit's custody through Copper Clearloop, precisely in preparation for this scenario.
No USD-backed spot funds are held on any exchange, including Bybit. Currently, the total unrealized gains (PNL) related to Bybit's hedge position are less than $30 million, far below half of the reserve fund. USDe is still fully overcollateralized. Further updates will be provided upon receiving more information."
ZachXBT: Bybit Hacker Sends 10,000 ETH to 39 New Addresses, Urges Swift Blacklisting
ZachXBT stated that the Bybit hacker has dispersed 10,000 ETH to 39 new addresses. "If you are an exchange platform or service provider, please blacklist these addresses on all EVM chains."

SlowMist Cosmos: Bybit Hack Technique Similar to North Korean Hackers
SlowMist founder Cosmos posted, "Although there is no clear evidence at the moment, judging from the 'Safe' multisig technique and the current money laundering technique, it looks like the work of North Korean hackers."
February 21
Bybit Hacker Has Started Distributing Funds to Multiple Addresses
At 23:57, according to Arkham Monitoring, the Bybit hacker has started distributing funds to multiple addresses.
Bybit CEO: Platform Withdrawals Normal, All Other Cold and Hot Wallets Unaffected; Bybit Solvent and Can Cover This Loss
At 23:53, Bybit CEO Ben Zhou updated stating that Bybit's hot wallet, warm wallet, and all other cold wallets were unaffected. The only wallet affected by the hack was the ETH cold wallet. All withdrawals are functioning normally. He also emphasized, "Bybit is still solvent, and even if the loss from this hack cannot be recovered, all customer assets remain 1:1 backed, and we can cover this loss."
Bybit Platform Total Assets at $15.727 Billion, Ethereum Assets Reach $5.18 Billion
As of February 21 at 23:54, according to Defillama data, Bybit's total platform assets amount to $15.727 billion, including:
· $6.263 billion in Bitcoin;
· $5.18 billion in Ethereum;
· $1.35 billion in SOL;
· $1.143 billion in TRON.
Bybit CEO: Hacker Controls Specific ETH Cold Wallet, All Other Cold Wallets Secure and Withdrawals Normal
At 23:44, Bybit Co-Founder and CEO Ben Zhou stated, "Bybit's ETH multisig cold wallet conducted a transfer to our hot wallet approximately 1 hour ago. This transaction appears to have been spoofed, with all signers seeing a spoofed interface showing the correct address and the URL coming from Safe.
However, the signature data was to change the logic of our ETH cold wallet's smart contract. This resulted in the hacker controlling a specific ETH cold wallet we signed for and moving all ETH in the wallet to this unconfirmed address."
Rest assured, all other cold wallets are secure. All withdrawals are normal. I will continue to update as more information becomes available. I would be grateful if any teams could help us trace the stolen funds.
Bybit Multi-Signature Address Moves $1.5 Billion Worth of ETH, Swaps LSD Assets for Native ETH via DEX
A few minutes later, crypto KOL Finish posted that according to on-chain data, a Bybit multi-signature address moved $1.5 billion worth of ETH to a new address. The funds arrived at the new address 0x47666fab8bd0ac7003bce3f5c3585383f09486e2, then were transferred to 0xa4b2fd68593b6f34e51cb9edb66e71c1b4ab449e, where 0xa4 is currently selling stETH and mETH in exchange for ETH.
「Currently, this address is using 4 different DEXs. If they were just swapping LSD for native ETH, the trade execution impact would be very bad (high slippage). This scale is usually done OTC, so this is very unusual.」
Zachxbt Monitors Suspicious Fund Outflows from Bybit
Around 11:27 PM on February 21st, Zachxbt Monitoring Channel stated that they are currently monitoring suspicious funds flowing out of Bybit, totaling over $14.6 billion.
Welcome to join the official BlockBeats community:
Telegram Subscription Group: https://t.me/theblockbeats
Telegram Discussion Group: https://t.me/BlockBeats_App
Official Twitter Account: https://twitter.com/BlockBeatsAsia











